The Importance Of Password Security
Although easy to remember, weak passwords are also easy to discover, being one of the most common targets of cyber criminals.
Most passwords are easy to be figured out when hackers apply what is called “brute force attacks” and make use of databases or password dictionaries, where attackers input information regarding their future victims.
There are a lot of dictionaries dealing with different languages, cultures, industries or hobbies, and hackers can find out sensible information about users quite easily – date of birth, name of spouse, names of children or pets, favourite sports team, the last pages you’ve navigated on the internet, and what kind of contact you like.
In other words, it’s hard to escape once a hacker is on your trail, therefore, preventive practices should be considered. A strong, unique password represent not only a preventive practice, but a strong defence against hacking.
How are Passwords discovered?
Attackers and hackers use a diversity of approaches and techniques to reveal passwords, by exploiting a range of social and technical vulnerabilities, such as:
tricking someone into revealing their password via social engineering (including phishing and coercion)
using the passwords leaked from data breaches to attack other systems where users have used the same password.
password spraying (using a small number of commonly used passwords in an attempt to access a large number of accounts)
brute-force attacks (the automated guessing of large numbers of passwords until the correct one is found)
theft of a password hash file, where the hash can be broken to recover the original passwords.
‘Shoulder surfing’ (observing someone typing in their password)
finding passwords which have been stored insecurely, such as sticky notes kept close to a device, or documents stored on devices.
manual password guessing (perhaps using personal information ‘cribs’ such as name, date of birth, or pet names)
intercepting a password (or password hash) as it is transmitted over a network.
installing a keylogger to intercept passwords when they are entered into a device
These techniques are widely available and documented on the internet, and many use automated tools requiring only moderate technical skills. National Cyber Security Centre
Below you will see the Top 25 most common passwords, by year. As you can easily notice, these passwords are quite simple to break by mediocre hackers.
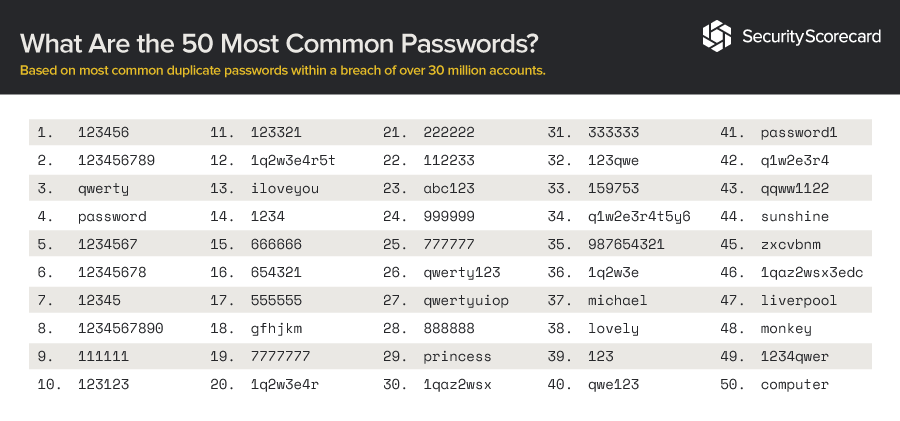
Password that don't break easily
A smart way to keep your digital accounts protected is to use a password generator, or to establish a password that is at least 8 characters long that do not resemble any personal information (your real name, company name, favorite team, pet’s name, etc), but that does include different types of characters – numbers, symbols, uppercase and lowercase letters, and space.
We provide IT Support in the West Midlands













